| |
 |
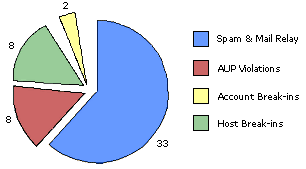
The chart below provides a snapshot of the computer and network security incidents that were reported on campus in the months of July and August. "Many incidents go unreported, so the numbers are not truly accurate," says Doreen Meyer, programmer with IT-DCAS and Incident Response and Reporting Project Manager. "They are meant to reinforce in all of us the sense that security incidents do occur on our campus," says Meyer. Some incidents generated more mail than others. "The winner was a mail relay incident that generated 55 complaints." The Incident Response and Reporting group has started to gather security statistics on a regular basis. We will publish them in the IT Times as they become available. For more information on the Incident Response and Reporting Project, see the Security Web site at http://security.ucdavis.edu/.
Note: In addition to the security incidents depicted in the figure, an average of 2.5 port scans were reported daily. Port scans are scans of the entire UCD network, generally looking for exploitable system weaknesses.
|